#middleware implementation
Explore tagged Tumblr posts
Text
Explore the key business challenges in Middleware Migration and how Jade Global can help you modernize your Middleware Systems.
1 note
·
View note
Text
This Week in Rust 593
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on X (formerly Twitter) or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Want TWIR in your inbox? Subscribe here.
Updates from Rust Community
Newsletters
The Embedded Rustacean Issue #42
This Week in Bevy - 2025-03-31
Project/Tooling Updates
Fjall 2.8
EtherCrab, the pure Rust EtherCAT MainDevice, version 0.6 released
A process for handling Rust code in the core kernel
api-version: axum middleware for header based version selection
SALT: a VS Code Extension, seeking participants in a study on Rust usabilty
Observations/Thoughts
Introducing Stringleton
Rust Any Part 3: Finally we have Upcasts
Towards fearless SIMD, 7 years later
LLDB's TypeSystems: An Unfinished Interface
Mutation Testing in Rust
Embedding shared objects in Rust
Rust Walkthroughs
Architecting and building medium-sized web services in Rust with Axum, SQLx and PostgreSQL
Solving the ABA Problem in Rust with Hazard Pointers
Building a CoAP application on Ariel OS
How to Optimize your Rust Program for Slowness: Write a Short Program That Finishes After the Universe Dies
Inside ScyllaDB Rust Driver 1.0: A Fully Async Shard-Aware CQL Driver Using Tokio
Building a search engine from scratch, in Rust: part 2
Introduction to Monoio: A High-Performance Rust Runtime
Getting started with Rust on Google Cloud
Miscellaneous
An AlphaStation's SROM
Real-World Verification of Software for Cryptographic Applications
Public mdBooks
[video] Networking in Bevy with ECS replication - Hennadii
[video] Intermediate Representations for Reactive Structures - Pete
Crate of the Week
This week's crate is candystore, a fast, persistent key-value store that does not require LSM or WALs.
Thanks to Tomer Filiba for the self-suggestion!
Please submit your suggestions and votes for next week!
Calls for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization.
If you are a feature implementer and would like your RFC to appear in this list, add a call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
No calls for testing were issued this week by Rust, Rust language RFCs or Rustup.
Let us know if you would like your feature to be tracked as a part of this list.
Call for Participation; projects and speakers
CFP - Projects
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
If you are a Rust project owner and are looking for contributors, please submit tasks here or through a PR to TWiR or by reaching out on X (formerly Twitter) or Mastodon!
CFP - Events
Are you a new or experienced speaker looking for a place to share something cool? This section highlights events that are being planned and are accepting submissions to join their event as a speaker.
* Rust Conf 2025 Call for Speakers | Closes 2025-04-29 11:59 PM PDT | Seattle, WA, US | 2025-09-02 - 2025-09-05
If you are an event organizer hoping to expand the reach of your event, please submit a link to the website through a PR to TWiR or by reaching out on X (formerly Twitter) or Mastodon!
Updates from the Rust Project
438 pull requests were merged in the last week
Compiler
allow defining opaques in statics and consts
avoid wrapping constant allocations in packed structs when not necessary
perform less decoding if it has the same syntax context
stabilize precise_capturing_in_traits
uplift clippy::invalid_null_ptr_usage lint as invalid_null_arguments
Library
allow spawning threads after TLS destruction
override PartialOrd methods for bool
simplify expansion for format_args!()
stabilize const_cell
Rustdoc
greatly simplify doctest parsing and information extraction
rearrange Item/ItemInner
Clippy
new lint: char_indices_as_byte_indices
add manual_dangling_ptr lint
respect #[expect] and #[allow] within function bodies for missing_panics_doc
do not make incomplete or invalid suggestions
do not warn about shadowing in a destructuring assigment
expand obfuscated_if_else to support {then(), then_some()}.unwrap_or_default()
fix the primary span of redundant_pub_crate when flagging nameless items
fix option_if_let_else suggestion when coercion requires explicit cast
fix unnested_or_patterns suggestion in let
make collapsible_if recognize the let_chains feature
make missing_const_for_fn operate on non-optimized MIR
more natural suggestions for cmp_owned
collapsible_if: prevent including preceeding whitespaces if line contains non blanks
properly handle expansion in single_match
validate paths in disallowed_* configurations
Rust-Analyzer
allow crate authors to control completion of their things
avoid relying on block_def_map() needlessly
fix debug sourceFileMap when using cppvsdbg
fix format_args lowering using wrong integer suffix
fix a bug in orphan rules calculation
fix panic in progress due to splitting unicode incorrectly
use medium durability for crate-graph changes, high for library source files
Rust Compiler Performance Triage
Positive week, with a lot of primary improvements and just a few secondary regressions. Single big regression got reverted.
Triage done by @panstromek. Revision range: 4510e86a..2ea33b59
Summary:
(instructions:u) mean range count Regressions ❌ (primary) - - 0 Regressions ❌ (secondary) 0.9% [0.2%, 1.5%] 17 Improvements ✅ (primary) -0.4% [-4.5%, -0.1%] 136 Improvements ✅ (secondary) -0.6% [-3.2%, -0.1%] 59 All ❌✅ (primary) -0.4% [-4.5%, -0.1%] 136
Full report here.
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
No RFCs were approved this week.
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
Tracking Issues & PRs
Rust
Tracking Issue for slice::array_chunks
Stabilize cfg_boolean_literals
Promise array::from_fn is generated in order of increasing indices
Stabilize repr128
Stabilize naked_functions
Fix missing const for inherent pointer replace methods
Rust RFCs
core::marker::NoCell in bounds (previously known an [sic] Freeze)
Cargo,
Stabilize automatic garbage collection.
Other Areas
No Items entered Final Comment Period this week for Language Team, Language Reference or Unsafe Code Guidelines.
Let us know if you would like your PRs, Tracking Issues or RFCs to be tracked as a part of this list.
New and Updated RFCs
Allow &&, ||, and ! in cfg
Upcoming Events
Rusty Events between 2025-04-02 - 2025-04-30 🦀
Virtual
2025-04-02 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2025-04-03 | Virtual (Nürnberg, DE) | Rust Nurnberg DE
Rust Nürnberg online
2025-04-03 | Virtual | Ardan Labs
Communicate with Channels in Rust
2025-04-05 | Virtual (Kampala, UG) | Rust Circle Meetup
Rust Circle Meetup
2025-04-08 | Virtual (Dallas, TX, US) | Dallas Rust User Meetup
Second Tuesday
2025-04-10 | Virtual (Berlin, DE) | Rust Berlin
Rust Hack and Learn
2025-04-15 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful
2025-04-16 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2025-04-17 | Virtual and In-Person (Redmond, WA, US) | Seattle Rust User Group
April, 2025 SRUG (Seattle Rust User Group) Meetup
2025-04-22 | Virtual (Dallas, TX, US) | Dallas Rust User Meetup
Fourth Tuesday
2025-04-23 | Virtual (Cardiff, UK) | Rust and C++ Cardiff
**Beyond embedded - OS development in Rust **
2025-04-24 | Virtual (Berlin, DE) | Rust Berlin
Rust Hack and Learn
2025-04-24 | Virtual (Charlottesville, VA, US) | Charlottesville Rust Meetup
Part 2: Quantum Computers Can’t Rust-Proof This!"
Asia
2025-04-05 | Bangalore/Bengaluru, IN | Rust Bangalore
April 2025 Rustacean meetup
2025-04-22 | Tel Aviv-Yafo, IL | Rust 🦀 TLV
In person Rust April 2025 at Braavos in Tel Aviv in collaboration with StarkWare
Europe
2025-04-02 | Cambridge, UK | Cambridge Rust Meetup
Monthly Rust Meetup
2025-04-02 | Köln, DE | Rust Cologne
Rust in April: Rust Embedded, Show and Tell
2025-04-02 | München, DE | Rust Munich
Rust Munich 2025 / 1 - hybrid
2025-04-02 | Oxford, UK | Oxford Rust Meetup Group
Oxford Rust and C++ social
2025-04-02 | Stockholm, SE | Stockholm Rust
Rust Meetup @Funnel
2025-04-03 | Oslo, NO | Rust Oslo
Rust Hack'n'Learn at Kampen Bistro
2025-04-08 | Olomouc, CZ | Rust Moravia
3. Rust Moravia Meetup (Real Embedded Rust)
2025-04-09 | Girona, ES | Rust Girona
Rust Girona Hack & Learn 04 2025
2025-04-09 | Reading, UK | Reading Rust Workshop
Reading Rust Meetup
2025-04-10 | Karlsruhe, DE | Rust Hack & Learn Karlsruhe
Karlsruhe Rust Hack and Learn Meetup bei BlueYonder
2025-04-15 | Leipzig, DE | Rust - Modern Systems Programming in Leipzig
Topic TBD
2025-04-15 | London, UK | Women in Rust
WIR x WCC: Finding your voice in Tech
2025-04-19 | Istanbul, TR | Türkiye Rust Community
Rust Konf Türkiye
2025-04-23 | London, UK | London Rust Project Group
Fusing Python with Rust using raw C bindings
2025-04-24 | Aarhus, DK | Rust Aarhus
Talk Night at MFT Energy
2025-04-24 | Edinburgh, UK | Rust and Friends
Rust and Friends (evening pub)
2025-04-24 | Manchester, UK | Rust Manchester
Rust Manchester April Code Night
2025-04-25 | Edinburgh, UK | Rust and Friends
Rust and Friends (daytime coffee)
2025-04-29 | Paris, FR | Rust Paris
Rust meetup #76
North America
2025-04-03 | Chicago, IL, US | Chicago Rust Meetup
Rust Happy Hour
2025-04-03 | Montréal, QC, CA | Rust Montréal
April Monthly Social
2025-04-03 | Saint Louis, MO, US | STL Rust
icu4x - resource-constrained internationalization (i18n)
2025-04-06 | Boston, MA, US | Boston Rust Meetup
Kendall Rust Lunch, Apr 6
2025-04-08 | New York, NY, US | Rust NYC
Rust NYC: Building a full-text search Postgres extension in Rust
2025-04-10 | Portland, OR, US | PDXRust
TetaNES: A Vaccination for Rust—No Needle, Just the Borrow Checker
2025-04-14 | Boston, MA, US | Boston Rust Meetup
Coolidge Corner Brookline Rust Lunch, Apr 14
2025-04-17 | Nashville, TN, US | Music City Rust Developers
Using Rust For Web Series 1 : Why HTMX Is Bad
2025-04-17 | Redmond, WA, US | Seattle Rust User Group
April, 2025 SRUG (Seattle Rust User Group) Meetup
2025-04-23 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
2025-04-25 | Boston, MA, US | Boston Rust Meetup
Ball Square Rust Lunch, Apr 25
Oceania
2025-04-09 | Sydney, NS, AU | Rust Sydney
Crab 🦀 X 🕳️🐇
2025-04-14 | Christchurch, NZ | Christchurch Rust Meetup Group
Christchurch Rust Meetup
2025-04-22 | Barton, AC, AU | Canberra Rust User Group
April Meetup
South America
2025-04-03 | Buenos Aires, AR | Rust en Español
Abril - Lambdas y más!
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
If you write a bug in your Rust program, Rust doesn’t blame you. Rust asks “how could the compiler have spotted that bug”.
– Ian Jackson blogging about Rust
Despite a lack of suggestions, llogiq is quite pleased with his choice.
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, U007D, joelmarcey, mariannegoldin, bennyvasquez, bdillo
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
2 notes
·
View notes
Text
Protect Your Laravel Application from Clickjacking Attacks
In today's digital landscape, protecting your web application from various security threats is crucial. One such threat is Clickjacking, an attack that tricks users into clicking on invisible or disguised elements on a webpage. For developers using the Laravel framework, ensuring your application is safe from clickjacking is essential.

In this post, we'll explore what clickjacking is and how to prevent it in your Laravel application. Plus, we’ll show you how to use our free Website Security Checker tool to assess potential vulnerabilities.
What is Clickjacking?
Clickjacking is a type of attack where malicious users embed your webpage into an invisible iframe on their site. The attacker then tricks the victim into clicking on the iframe, which can lead to unwanted actions like changing settings, submitting forms, or even transferring funds without their knowledge.
For example, a button that looks harmless on the surface might trigger an action you didn’t intend to take when clicked in an iframe. This type of attack can be devastating for your users’ privacy and your application’s security.
Preventing Clickjacking in Laravel
Fortunately, Laravel provides a straightforward way to mitigate the risk of clickjacking. Here's how you can do it:
Step 1: Use HTTP Headers
The best way to prevent clickjacking in your Laravel application is by setting proper HTTP headers. You can do this by adding the X-Frame-Options header to your application's response. This header tells the browser not to allow your webpage to be embedded in an iframe.
In Laravel, you can add this header globally by modifying the app/Http/Middleware/VerifyCsrfToken.php file.
Here’s how you can modify the middleware:
// app/Http/Middleware/VerifyCsrfToken.php namespace App\Http\Middleware; use Closure; use Illuminate\Http\Request; class VerifyCsrfToken { public function handle(Request $request, Closure $next) { // Adding X-Frame-Options header to prevent clickjacking response()->headers->set('X-Frame-Options', 'DENY'); return $next($request); } }
With this code, the header X-Frame-Options: DENY ensures that no website can embed your pages in an iframe. If you want to allow only certain websites to embed your content, you can use SAMEORIGIN instead of DENY.
Step 2: Use Content Security Policy (CSP)
Another robust method to prevent clickjacking attacks is by using a Content Security Policy (CSP). Laravel supports CSP through middleware. By setting a strict policy, you can specify exactly which websites are allowed to load your pages in an iframe.
Here’s an example of how you can configure the CSP in your Laravel application:
// app/Http/Middleware/ContentSecurityPolicy.php namespace App\Http\Middleware; use Closure; use Illuminate\Http\Request; class ContentSecurityPolicy { public function handle(Request $request, Closure $next) { // Setting a strict CSP header response()->headers->set('Content-Security-Policy', "frame-ancestors 'none';"); return $next($request); } }
This ensures that no site can embed your application within an iframe.
Why Use Our Free Website Security Checker?
After implementing these preventive measures, it’s important to test your application’s security. Our free Website Security Scanner tool provides a comprehensive vulnerability assessment for your website, including tests for clickjacking and other security issues.
Here’s a screenshot of our free tool in action:

Screenshot of the free tools webpage where you can access security assessment tools.
Conclusion
Securing your Laravel application against clickjacking attacks is crucial for protecting your users and ensuring your web app remains safe. By following the steps outlined above, you can significantly reduce the risk of such attacks. Additionally, our free Website Security Checker can help you ensure that your site is not vulnerable to clickjacking or any other security issues.
And here’s an example of the vulnerability assessment report generated by our free tool:

An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
By regularly using security tools and following best practices, you can enhance your website’s defenses and maintain a safe browsing environment for your users.
Take Action Today
Start testing your website with our free tool to test website security free and take the first step in protecting your site from clickjacking and other cyber threats.
#Clickjacking#laravel#cyber security#cybersecurity#data security#pentesting#security#the security breach show
3 notes
·
View notes
Link
#ASP.NET#ASP.NETCore#ASP.NETCorerouting#HTTPRedirect#HttpRequest#HTTPResponse#MVC#RazorPages#Requestpipeline#Views#WorkInProgress
2 notes
·
View notes
Text
Built-in Logging with Serilog: How EasyLaunchpad Keeps Debugging Clean and Insightful

Debugging shouldn’t be a scavenger hunt.
When things break in production or behave unexpectedly in development, you don’t have time to dig through vague error messages or guess what went wrong. That’s why logging is one of the most critical — but often neglected — parts of building robust applications.
With EasyLaunchpad, logging is not an afterthought.
We’ve integrated Serilog, a powerful and structured logging framework for .NET, directly into the boilerplate so developers can monitor, debug, and optimize their apps from day one.
In this post, we’ll explain how Serilog is implemented inside EasyLaunchpad, why it’s a developer favorite, and how it helps you launch smarter and maintain easier.
🧠 Why Logging Matters (Especially in Startups)
Whether you’re launching a SaaS MVP or maintaining a production application, logs are your eyes and ears:
Track user behavior
Monitor background job status
Catch and analyze errors
Identify bottlenecks or API failures
Verify security rules and access patterns
With traditional boilerplates, you often need to configure and wire this up yourself. But EasyLaunchpad comes preloaded with structured, scalable logging using Serilog, so you’re ready to go from the first line of code.
🔧 What Is Serilog?
Serilog is one of the most popular logging libraries for .NET Core. Unlike basic logging tools that write unstructured plain-text logs, Serilog generates structured logs — which are easier to search, filter, and analyze in any environment.
It supports:
JSON log output
File, Console, or external sinks (like Seq, Elasticsearch, Datadog)
Custom formats and enrichers
Log levels: Information, Warning, Error, Fatal, and more
Serilog is lightweight, flexible, and production-proven — ideal for modern web apps like those built with EasyLaunchpad.
🚀 How Serilog Is Integrated in EasyLaunchpad

When you start your EasyLaunchpad-based project, Serilog is already:
Installed via NuGet
Configured via appsettings.json
Injected into the middleware pipeline
Wired into all key services (auth, jobs, payments, etc.)
🔁 Configuration Example (appsettings.json):
“Serilog”: {
“MinimumLevel”: {
“Default”: “Information”,
“Override”: {
“Microsoft”: “Warning”,
“System”: “Warning”
}
},
“WriteTo”: [
{ “Name”: “Console” },
{
“Name”: “File”,
“Args”: {
“path”: “Logs/log-.txt”,
“rollingInterval”: “Day”
}
}
}
}
This setup gives you daily rotating log files, plus real-time console logs for development mode.
🛠 How It Helps Developers
✅ 1. Real-Time Debugging
During development, logs are streamed to the console. You’ll see:
Request details
Controller actions triggered
Background job execution
Custom messages from your services
This means you can debug without hitting breakpoints or printing Console.WriteLine().
✅ 2. Structured Production Logs
In production, logs are saved to disk in a structured format. You can:
Tail them from the server
Upload them to a logging platform (Seq, Datadog, ELK stack)
Automatically parse fields like timestamp, level, message, exception, etc.
This gives predictable, machine-readable logging — critical for scalable monitoring.
✅ 3. Easy Integration with Background Jobs
EasyLaunchpad uses Hangfire for background job scheduling. Serilog is integrated into:
Job execution logging
Retry and failure logs
Email queue status
Error capturing
No more “silent fails” in background processes — every action is traceable.
✅ 4. Enhanced API Logging (Optional Extension)
You can easily extend the logging to:
Log request/response for APIs
Add correlation IDs
Track user activity (e.g., login attempts, failed validations)
The modular architecture allows you to inject loggers into any service or controller via constructor injection.
🔍 Sample Log Output
Here’s a typical log entry generated by Serilog in EasyLaunchpad:
{
“Timestamp”: “2024–07–10T08:33:21.123Z”,
“Level”: “Information”,
“Message”: “User {UserId} logged in successfully.”,
“UserId”: “5dc95f1f-2cc2–4f8a-ae1b-1d29f2aa387a”
}
This is not just human-readable — it’s machine-queryable.
You can filter logs by UserId, Level, or Timestamp using modern logging dashboards or scripts.
🧱 A Developer-Friendly Logging Foundation
Unlike minimal templates, where you have to integrate logging yourself, EasyLaunchpad is:
Ready-to-use from first launch
Customizable for your own needs
Extendable with any Serilog sink (e.g., database, cloud services, Elasticsearch)
This means you spend less time configuring and more time building and scaling.
🧩 Built-In + Extendable
You can add additional log sinks in minutes:
Log.Logger = new LoggerConfiguration()
.WriteTo.Console()
.WriteTo.File(“Logs/log.txt”)
.WriteTo.Seq(“http://localhost:5341")
.CreateLogger();
Want to log in to:
Azure App Insights?
AWS CloudWatch?
A custom microservice?
Serilog makes it possible, and EasyLaunchpad makes it easy to start.
💼 Real-World Scenarios
Here are some real ways logging helps EasyLaunchpad-based apps:
Use Case and the Benefit
Login attempts — Audit user activity and failed attempts
Payment errors- Track Stripe/Paddle API errors
Email queue- Debug failed or delayed emails
Role assignment- Log admin actions for compliance
Cron jobs- Monitor background jobs in real-time
🧠 Final Thoughts
You can’t fix what you can’t see.
Whether you’re launching an MVP or running a growing SaaS platform, structured logging gives you visibility, traceability, and peace of mind.
EasyLaunchpad integrates Serilog from day one — so you’re never flying blind. You get a clean, scalable logging system with zero setup required.
No more guesswork. Just clarity.
👉 Start building with confidence. Check out EasyLaunchpad at https://easylaunchpad.com and see how production-ready logging fits into your stack.
#Serilog .NET logging#structured logs .NET Core#developer-friendly logging in boilerplate#.net development#saas starter kit#saas development company#app development#.net boilerplate
1 note
·
View note
Text
SELinux in AOSP: A Guide to Securing Embedded Android Systems
Introduction
Security-Enhanced Linux (SELinux) is a core security mechanism in the Android Open Source Project (AOSP) that enforces robust access control. Unlike traditional Discretionary Access Control (DAC), which relies on user-based permissions, SELinux uses Mandatory Access Control (MAC) to restrict system interactions based on predefined policies. Android integrated SELinux starting from version 4.3. It runs in either permissive mode, which logs violations, or enforcing mode, which blocks unauthorized actions.

Understanding SELinux policies, labels, and domains is essential for embedded developers working on middleware, HAL, and system daemons in order to secure Android devices. Sensitive system components are protected, unauthorized access is limited, and privilege escalation is avoided with proper SELinux configuration. This blog discusses best practices for creating security policies, how SELinux functions within AOSP, and a real-world example of using SELinux on a binderized HAL. Developers can strengthen embedded systems against exploits and security breaches by becoming proficient with SELinux.
What is SELinux?
With mandatory access control (MAC) policies that limit programs' capabilities beyond conventional discretionary access controls (DAC), SELinux is a security architecture built into the Linux kernel. It guarantees that an application's activities stay contained within predetermined bounds even in the event that it is compromised.
Core Concepts of SELinux
Labels: Every process and object (like files, directories, and ports) in the system is assigned a security label. A key component of SELinux's decision-making process is these labels.
Type Enforcement (TE): The main SELinux mechanism is Type Enforcement (TE), in which policies specify how types (labels) linked to objects and processes can communicate. A process named httpd_t (Apache), for example, can be made to only access files with the label httpd_sys_content_t.
Roles and Users: To manage permissions more precisely, SELinux defines roles and users. Nonetheless, type enforcement continues to be the main focus in many implementations.
SELinux in AOSP
SELinux integration with Android
Google strengthened Android's security by integrating SELinux into the platform starting with version 4.3. SELinux functions in two ways in AOSP:
Permissive Mode: Violators are recorded but not stopped; SELinux rules are not enforced.
Enforcing Mode: SELinux rules are put into effect, and infractions are recorded and prevented. For strong security, Android devices try to run in enforcing mode.
Advantages of SELinux in Android
Privilege escalation is mitigated: SELinux restricts an application's behavior even if it acquires unauthorized privileges, avoiding more widespread system compromises.
Protection Against Malware: By limiting applications' access to private information or system components, SELinux policies can lessen the possible impact of malware.
Enhanced Multi-User Security: SELinux makes sure that user data is kept separate and safe from other users and applications by implementing stringent access controls.
Implementing SELinux in AOSP
Configuring the Linux kernel for SELinux: Make sure the kernel is compiled with SELinux support. This entails turning on particular security module configuration options.
Filesystem Labeling: Give filesystem objects the proper security labels. This can be accomplished by setting default labels in filesystem images or by using tools such as restorecon.
Compilation of Policies: Using tools like checkpolicy, create SELinux policies that are specific to the needs of your system.
Policy Loading: Use tools like load_policy or incorporate the compiled policies into the system's initialization procedure to load them into the kernel.
Writing SELinux Policies
IVI (In-Vehicle Infotainment), ADAS (Advanced Driver Assistance Systems), and telematics are among the vital services that Android Automotive OS (AAOS) manages in automotive embedded systems. SELinux policies are necessary to enforce stringent access controls across all system components, especially middleware services, Binderized HALs, and system daemons, in order to ensure security in such a system. In order to make sure that only authorized system components can access and alter vehicle data, we'll map SELinux policy writing to a real-world automotive example below using a binderized HAL.
Determine Types and Domains
Consider a Vehicle HAL (VHAL) in an automotive system, which gives users access to information about the vehicle, including its speed, fuel level, engine status, and door lock condition. The telematics module, navigation app, and IVI system are among the system elements with which the Vehicle HAL service communicates.
The hal_vehicle_t domain is where the Vehicle HAL daemon operates.
vehicle_data_t is the label for vehicle data files.
The ivi_system_t domain is where the IVI system operates.
The telematics_t domain is where the Telematics service functions.
By defining these domains, unauthorized applications are prevented from accessing vital vehicle parameters and controlled access between various system components is ensured.
Tools and Resources
SELinux Notebook: An open-source resource that provides comprehensive insights into SELinux concepts and implementations. GitHub - SELinuxProject/selinux-notebook
NSA's SELinux Implementation Report: An in-depth report detailing the implementation of SELinux as a Linux Security Module. Implementing SELinux as a Linux Security Module
Conclusion
With SELinux included in AOSP, developers can implement strict access controls, isolate processes, and keep sensitive information safe.
Whether you're building embedded Android systems, HAL layers, or automotive and IoT device middleware, SELinux offers a secure framework to ensure system integrity.
For any solution related to SELinux implementation, HAL hardening, or embedded Android security, connect with Silicon Signals at www.siliconsignals.io or email us at [email protected]. 👉 Do follow us on LinkedIn to stay updated on embedded tech insights and innovations.
#linux kernel#androidbsp#linuxdebugging#android#aosp#embeddedtechnology#embeddedsoftware#embeddedsystems#iot development services#selinux#linuxsecurity#aospsecurity
0 notes
Text
Digital Integration Solutions with Cloud-Based Architectural Design
W3 Partnership, founded in 2007, provides solutions and services that help organizations make sense of their digital applications and services through integrated platforms and patterns. SMEs in their respective fields, our in-house integration consultants are specialists in IBM and MuleSoft products, and our cloud consultants and developers are experts in AWS and Azure. We design, develop, manage, and monitor such platforms.
At W3 Partnership, we specialize in delivering integration connectivity as a service (iCaaS), cloud-based integration solutions, and middleware integration consultancy tailored to your unique needs. With decades of expertise, we empower businesses to streamline operations, eliminate silos, and drive innovation through hybrid integration platforms and advanced digital integration architecture services. Using advanced requirements analysis and digital integration architecture techniques, we collect all the necessary information to enable efficient stakeholder communication, ensuring a smooth transition from analysis to implementation.
Architecture Digital Integration
A data architecture called a Digital Integration Hub (DIH) separates the digital applications of the SoRs and compiles operational data into a low-latency data fabric. Organizations may connect to, integrate, and manage various software applications and systems using this architecture. To simplify data exchange and automate business processes, Architecture digital integration provides a central hub for managing the data flow between different systems. A digital integration hub supports modernization efforts by delivering a detached API layer that easily supports current online apps.
Digital Integration Solutions
An organization's digital transformation journey heavily depends on integrations to create a connected business. With the potent combination of innovative integration tools, intelligent methodologies, tried and tested templates, carefully designed organizational frameworks, and our knowledge and experience. Technology solutions known as "digital integration solutions" make it easier for digital systems, apps, and data sources to communicate and exchange data. They give firms a capacity to integrate many systems, optimize processes, and use data from various sources to make better decisions and provide better customer service.
Cloud-Based Integration
In today's digital-first business world, cloud-based integration serves as the cornerstone for tying together systems, data, and applications. Our cloud-based integration services at W3 Partnership effectively connect on-premises systems, cloud applications, and third-party solutions to form a cohesive digital ecosystem. Our solutions, built with agility, scalability, and security in mind, simplify IT, enhance data accuracy, and facilitate real-time data exchange, enabling your teams to make data-driven decisions more quickly. W3 Partnership's cloud-based integration strategy utilizes API-led connections and sophisticated integration platforms to help companies rapidly and affordably integrate apps. Our cloud-based integration services simplify the connection of marketing tools, CRM systems, ERP platforms, and data analytics applications while ensuring data accessibility and integrity.
1 note
·
View note
Text
Laravel Programming: A Comprehensive Guide
Table of Contents
Introduction to Laravel
Why Use Laravel?
Installing Laravel
Laravel Folder Structure
Routing and Controllers
Blade Templating Engine
Laravel Models and Eloquent ORM
Migrations and Database Seeding
Request Lifecycle and Middleware
Form Handling and Validation
Authentication and Authorization
Laravel Artisan CLI
RESTful API Development in Laravel
Testing in Laravel
Deployment and Performance Optimization
Laravel Ecosystem and Tools
Conclusion
1. Introduction to Laravel
Laravel is an open-source PHP framework built by Taylor Otwell. It follows the MVC (Model-View-Controller) architectural pattern, which promotes a clean separation between business logic, UI, and data.
Laravel aims to make development faster and easier by providing powerful tools such as:
Routing
Middleware
Authentication
Blade templating
ORM (Eloquent)
Queues
Artisan command-line tool
Laravel is currently one of the most popular PHP frameworks and powers thousands of web applications globally.
2. Why Use Laravel?
Benefits of Laravel:
Clean and Elegant Syntax: Laravel simplifies complex tasks.
MVC Architecture: Ensures separation of concerns.
Eloquent ORM: Elegant database abstraction layer.
Blade Templating: Lightweight yet powerful templating engine.
Built-in Authentication & Authorization: Secure and easy to implement.
Community and Ecosystem: Laravel has a rich ecosystem like Nova, Horizon, Forge, Envoyer, etc.
Testing Ready: PHPUnit integration for test-driven development (TDD).
0 notes
Text
Best Practices for API Integration in Next.js Apps
Modern web applications thrive on seamless, efficient, and secure API communication. Whether it's pulling data from a CMS, connecting with a payment gateway, or interacting with a cloud service, API integration is at the core of every high-performance Next.js app.
Next.js, with its server-side capabilities and built-in API routes, offers a flexible environment for creating and consuming APIs. But with flexibility comes the responsibility of integration best practices especially when dealing with sensitive data or mission-critical services.

Why Next.js Is Built for API-Driven Applications
Next.js offers both server-side and client-side rendering, making it ideal for hybrid API workflows. Developers can:
Use getServerSideProps() or getStaticProps() for SSR/SSG-based data fetching.
Utilize /api routes to implement backend logic directly within the app.
Take advantage of built-in middleware for authentication, error handling, and request filtering.
This architectural flexibility is why SaaS companies can scale frontend with Next.js, particularly when their APIs need to serve both dynamic dashboards and SEO-friendly landing pages.
Best Practices for Integrating APIs in Next.js
1. Centralize API Logic
Avoid scattering fetch calls across components. Instead, centralize them using a services directory or a custom hook (useApi) for consistency and maintainability.
2. Use Environment Variables
Secure API keys and sensitive data by using .env.local. Never hardcode tokens in the frontend codebase.
3. Handle Errors Gracefully
Build resilient error handling using try/catch blocks and conditionally render UI based on the state of the API response.
4. Use SWR or React Query
For client-side API calls, libraries like SWR (by Vercel) or React Query help manage caching, loading states, and automatic revalidation.
5. Secure Your APIs
Whether you're calling third-party APIs or building your own endpoints within the Next.js /api folder, security is critical. Learn how to ensure REST API security to prevent unauthorized access, data leaks, and common vulnerabilities like CSRF and XSS.
When Should You Hire an Expert?
As your application scales and API complexities increase especially with third-party integrations, real-time data, or sensitive business logic it’s beneficial to hire Next.js developers who are skilled in scalable architectures, secure integrations, and performance optimization.
Final Thoughts
APIs are the arteries of modern web apps. When combined with the server-side strengths of Next.js, your frontend becomes more powerful, reactive, and tailored to user needs. By following these best practices, you’re not only creating better experiences, you're building a scalable, secure, and resilient application foundation.
0 notes
Link
#AdaptiveSolutions#CollaborativeDevelopment#Cross-BorderSynergies#GovernanceFrameworks#IndustrialIntegration#Open-SourceAI#regionalinnovation#TechnologyReadiness
0 notes
Text

Integration Developer
Job SummaryWe are seeking a talented Integration Developer (8-10yrs) to join our team. If you're passionate about coding, problem-solving, and innovation, wed love to hear from you!About CodeVyasa: Were a fast-growing multinational software company with offices in Florida and New Delhi. Our clientele spans across the US, Australia, and the APAC region. Were proud to collaborate with Fortune 500 companies and offer opportunities to work alongside the top 0.1 percent of developers in the industry. Youll report to IIT/BITS graduates with over 10 years of development experience. Ready to elevate your career? Visit us at codevyasa.com. Key Responsibilities:
Design, develop, and implement integration solutions using Azure Integration Services (Logic Apps, API Management, Service Bus, Event Grid, Functions) or Boomi.
Develop and manage APIs, web services, and data pipelines to ensure seamless system communication.
Optimize integration workflows for high performance, scalability, and security.
Collaborate with cross-functional teams to understand integration needs and provide solutions.
Monitor, troubleshoot, and improve existing integration frameworks and middleware.
Implement best practices in API management, security, and authentication (OAuth, JWT, SAML, etc.).
Work with cloud-based and on-premise applications to develop robust hybrid integration solutions.
Ensure compliance with enterprise integration standards, governance, and security policies.
Automate deployment processes using CI/CD pipelines, DevOps practices, and Infrastructure-as-Code (IaC).
Stay up to date with emerging trends and technologies in cloud integration and API management.
Required Skills & Experience:
4+ years of experience in enterprise integration, API development, and middleware solutions.
Hands-on experience with Azure Integration Services (Logic Apps, Service Bus, Event Grid, Functions) or Boomi.
Strong expertise in API development, RESTful services, GraphQL, and SOAP-based integrations.
Experience with cloud platforms (Azure, AWS, GCP) and hybrid cloud integrations.
Strong knowledge of event-driven architectures, messaging queues (Kafka, RabbitMQ, Azure Service Bus, etc.).
Proficiency in authentication and security protocols (OAuth, SAML, JWT, SSL/TLS).
Experience in database integrations (SQL, NoSQL, Cosmos DB, MongoDB).
Hands-on experience with DevOps, CI/CD, containerization (Docker, Kubernetes), and Infrastructure-as-Code (Terraform, ARM templates).
Strong problem-solving and debugging skills in integration and middleware technologies.
Experience working with enterprise ERP, CRM, and SaaS applications is a plus.
Why Join CodeVyasa? Work on innovative, high-impact projects with a team of top-tier professionals.Continuous learning opportunities and professional growth.Flexible work environment with a supportive company culture.Competitive salary and comprehensive benefits package.Free healthcare coverage. Location- ChennaiBudget- upto 45-50lakhs Must Have skills- BOOMi (must have) + Azure integration services (Must have), Need Developers and not admin. Note: There are two different requirements- 1. Boomi Developer 2.Azure Developer
Job Type
Payroll
Categories
DevOps Engineers (Software and Web Development)
Middleware Developer (Software and Web Development)
Cloud Architects (Software and Web Development)
Software Engineer (Software and Web Development)
Data Engineer (Software and Web Development)
Must have Skills
Dell Boomi - 8 Years
Azure - 4 Years
API Development - 4 YearsIntermediate
GCP - 2 YearsIntermediate
AWS - 2 YearsIntermediate
Integration development - 4 YearsIntermediate
Apply Now: https://crazysolutions.in/job-openings/
0 notes
Text
Week 2 (Lecture Reflection) – Middleware and Implementation Systems / Ambience
Ambience is something that I don't excel at when it comes to sound design. Layering and manipulating a variety of wavetables has usually yielded decent results when sculpting hard leads or aggressive bass one-shots; yet, when I try to create a lush, atmospheric sequenced pad, I find it extremely hard not to dive straight into my preset folders. However, the material in today's lecture reminded me of a goal I had set a while back – to start designing sounds in other synths (not just Xfer Serum). Even though my sound design goal is derived from a more elementary approach, I still believe that hearing this alternative perspective is beneficial to any future attempts at Ambience.
0 notes
Text
Master API Versioning in Laravel 12!
Facing challenges with managing changes in your Laravel APIs? This comprehensive, step-by-step guide walks you through effective API versioning strategies in Laravel 12. Ensure smooth updates for your users and maintain a clean, organized codebase. Dive in and build robust, scalable APIs!
#LaravelTips #APIDevelopment #LaravelTutorial #WebDev #Programming #Coding #SoftwareDevelopment #TechGuide #LaravelCommunity #PHPDeveloper
0 notes
Text
A Step-by-Step Guide to Successful Salesforce Marketing Cloud Implementation

In today’s customer-first world, personalized and automated marketing is essential for building loyalty, increasing engagement, and driving conversions. Salesforce Marketing Cloud (SFMC) is one of the most powerful tools businesses can use to make that happen—but unlocking its full potential takes a thoughtful, strategic approach.
As an experienced Salesforce consultant in Sydney, I’ve helped many businesses across industries implement Salesforce Marketing Cloud effectively. Whether you're a mid-sized business or a large enterprise, this guide walks you through every essential phase of a successful implementation. Let’s dive in.
What Is Salesforce Marketing Cloud?
Salesforce Marketing Cloud is a digital marketing platform that helps businesses engage customers with the right message, at the right time, on the right channel. It includes tools for:
Email and mobile messaging
Customer journeys
Audience segmentation
Social media marketing
Advertising and analytics
AI-powered personalization with Einstein
However, to make SFMC work smoothly within your business ecosystem, you need the expertise of a reliable Salesforce consulting partner in Sydney to guide you through setup, integration, and optimization.
Step 1: Define Goals and Use Cases
Before jumping into setup, take time to define what you want to achieve. Salesforce Marketing Cloud is a robust platform, and knowing your business goals helps determine what features you’ll need.
Ask questions like:
Are you trying to increase email open rates?
Do you want to create a unified customer view?
Is real-time, behavior-based messaging a priority?
A Salesforce consultant in Sydney can help you map your objectives to specific Marketing Cloud modules, such as Journey Builder, Email Studio, or Audience Builder.
Step 2: Audit Your Existing Data and Systems
A successful SFMC implementation hinges on seamless data flow. This means taking stock of your current CRM, email tools, customer databases, and any third-party systems.
As part of our Salesforce consulting in Sydney, we typically assess:
Data quality: Is your customer data clean and up-to-date?
Data sources: Where is data currently stored?
Integrations: What platforms (e.g., Shopify, HubSpot, ERP) need to connect with SFMC?
This audit helps build a roadmap for integrations and ensures a single, unified customer view once Marketing Cloud is live.
Step 3: Build the Right Team
Marketing Cloud implementation isn’t just an IT project—it requires a cross-functional team. Ideally, your implementation team should include:
A Salesforce developer in Sydney to handle technical configurations and integrations
A marketing lead to align strategy
A data specialist to manage ETL processes
A project manager to oversee timelines
Working with a trusted Salesforce consulting partner in Sydney brings all of this expertise to your business without needing to hire a full-time team.
Step 4: Choose the Right Marketing Cloud Studios and Builders
Salesforce Marketing Cloud is modular. Depending on your goals, you’ll want to activate specific components like:
Email Studio: For personalized email campaigns
Journey Builder: To create automated, multi-step customer journeys
Mobile Studio: For SMS and push notifications
Social Studio: To manage and analyze social media channels
Advertising Studio: For audience targeting via Facebook, Google, LinkedIn
Einstein AI: For predictive insights and personalization
A seasoned Salesforce consultant in Sydney will help you select the right modules to avoid overspending or underutilizing your license.
Step 5: Integration with Salesforce CRM and Third-Party Platforms
Salesforce Marketing Cloud works best when it’s integrated with your existing Salesforce CRM or third-party platforms like ecommerce, payment gateways, or customer service tools.
This phase includes:
Setting up Marketing Cloud Connect to sync CRM and SFMC
Building APIs or middleware for third-party platforms
Configuring data extensions for unified customer profiles
If you’re using Sales Cloud or Service Cloud, a Salesforce developer in Sydney can ensure data synchronization between departments—so your sales, service, and marketing teams operate from the same source of truth.
Step 6: Create Segments and Audience Lists
Effective marketing starts with the right audience segmentation. With SFMC, you can build segments based on:
Demographics (age, gender, location)
Behavior (past purchases, email opens, site visits)
Lifecycle stage (lead, customer, repeat buyer)
Using Audience Builder and Contact Builder, we help clients define high-value segments for personalized messaging. Advanced segmentation powered by Einstein AI further improves targeting by predicting behavior and preferences.
Step 7: Design Campaigns and Journeys
Once your segments are defined, it’s time to design customer journeys and automated campaigns. This is where Salesforce Marketing Cloud really shines.
Use Journey Builder to:
Trigger emails based on customer behavior
Send SMS reminders after abandoned carts
Follow up with surveys post-purchase
Re-engage inactive users with special offers
With the help of expert Salesforce consultants in Sydney, these journeys can be mapped strategically to match customer lifecycle stages and business objectives.
Step 8: Test Everything
Before launching, run thorough QA on:
Email rendering across devices and inboxes
Journey logic and entry/exit criteria
Data syncing and field mapping
Unsubscribe and preference center functionality
A professional Salesforce consulting partner in Sydney ensures your campaigns run flawlessly and that all compliance requirements (like GDPR and CAN-SPAM) are met.
Step 9: Train Your Marketing Team
Your internal team needs to know how to use Salesforce Marketing Cloud efficiently. Training should include:
How to build and schedule email campaigns
How to analyze campaign performance
How to update customer journeys
How to use Einstein AI insights
A Salesforce consultant in Sydney can provide tailored, hands-on training sessions based on your specific SFMC configuration and business workflows.
Step 10: Monitor, Optimize, and Scale
Implementation doesn’t end with the first campaign launch. Continuous optimization is essential for long-term success.
Monitor key metrics like:
Open and click-through rates
Conversion rates by channel
Unsubscribes and bounce rates
Customer lifetime value
Use A/B testing and AI-powered recommendations to improve campaigns over time. Working with Salesforce consultants in Sydney ensures you keep adapting to changes in customer behavior and market trends.
Real-World Example: Retail Business in Sydney
We recently helped a Sydney-based retail chain transition from Mailchimp to Salesforce Marketing Cloud. Their goals were to:
Create personalized product recommendations
Automate welcome and re-engagement emails
Integrate marketing data with Salesforce CRM
The result?
A 36% increase in email engagement
22% growth in repeat purchases
A fully connected marketing and sales ecosystem
This transformation wouldn’t have been possible without custom integrations and journey design by a skilled Salesforce developer in Sydney.
Why Work With Salesforce Consultants in Sydney?
Salesforce Marketing Cloud is powerful—but complex. Partnering with a qualified Salesforce consulting partner in Sydney ensures:
Faster, smoother implementation
Customized integrations and automations
Regulatory compliance (GDPR, CAN-SPAM, etc.)
Ongoing strategy and support
Whether you're launching your first campaign or scaling across multiple regions, experienced Salesforce consultants in Sydney bring local expertise and global insights to your project.
Final Thoughts
Salesforce Marketing Cloud is a game-changer for businesses ready to deliver smarter, more personalized marketing. But to fully realize its potential, you need more than just licenses—you need a clear roadmap, proper integration, and expert support.
By following this step-by-step guide and partnering with a trusted Salesforce consultant in Sydney, your business can launch high-impact marketing campaigns that drive real ROI.
Ready to get started? Connect with our team of certified Salesforce developers and consultants in Sydney and take your marketing to the next level.
Read more https://medium.com/@codezix.seo/the-role-of-salesforce-marketing-cloud-in-automating-customer-engagement-90f20a9e9295
#salesforce consultant in sydney#salesforce consulting in sydney#salesforce consulting partner in sydney#salesforce consultants in sydney#salesforce developer in sydney#A Step-by-Step Guide to Successful Salesforce Marketing Cloud Implementation
0 notes
Text
How Android System Services Connect Apps and HAL: A Deep Dive
Android is more than just a mobile operating system—it's a powerful middleware that seamlessly connects apps to the underlying hardware through a layered architecture of frameworks, services, and abstraction layers. The Android System Services, which control essential features like window handling, power management, telephony, and more, are at the core of this framework. By serving as a bridge, these services guarantee seamless communication between the hardware abstraction layer (HAL), the framework, and user applications.
The internal operations of Android System Services are examined in this blog, along with how they interact with HAL and apps.
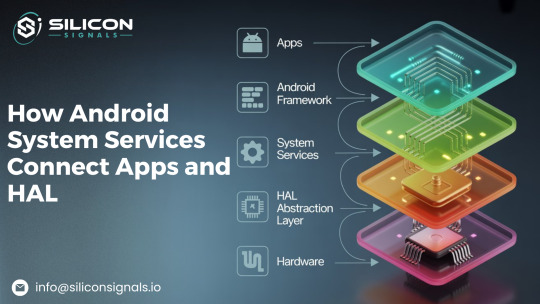
Understanding Android System Services
Essential parts of AOSP, Android System Services oversee fundamental features like power, connectivity, phone, and security. Through Binder IPC, these services enable smooth communication between applications, the framework, and hardware while operating inside SystemServer. Because each service is registered in ServiceManager, it is available throughout the system, including ActivityManagerService, PowerManagerService, and TelephonyService. By serving as go-betweens, system services make sure that applications communicate with hardware through the Hardware Abstraction Layer (HAL) without requiring direct access.
Comprehending these services aids developers in extending AOSP functionalities, improving performance, and troubleshooting issues while preserving security and modularity within the Android ecosystem.

Key Components of Android System Services
SystemServer: The process in charge of launching and overseeing essential system functions.
ServiceManager: A central registry that maintains a record of every system service that is available.
Binder IPC: Applications, framework elements, and system services can interact thanks to the communication mechanism known as Binder IPC.
HAL (Hardware Abstraction Layer): System services can communicate with hardware through the Hardware Abstraction Layer (HAL), which offers a common interface for hardware-specific implementations.

System Service Types
System services can be divided into groups according to how they work:
Core Services: ActivityManagerService, WindowManagerService, and PackageManagerService
Hardware Services: SensorService, AudioService, and PowerManagerService
Connectivity Services: Bluetooth, WiFi, and Telephony Services
Security Services: SELinuxManagerService and KeystoreService
Each system service registers with ServiceManager for worldwide accessibility and operates as a distinct thread or process inside SystemServer.

How System Services Interact with Apps and HAL
To understand system service interactions, let’s break it down into three communication flows:

1. Applications to System Services (Interaction at the Framework Layer)
Through the Android Framework APIs, an application can interact with the appropriate system service to carry out system-level tasks (like adjusting brightness or connecting to WiFi).
For instance, determining the battery level:
The BatteryManager API's getBatteryPercentage() method is invoked by the application.
BatteryManagerService receives the request and retrieves the most recent battery status.
The data is returned to the application by BatteryManagerService.
Important Takeaway: The application never communicates with the kernel or HAL directly. It always passes via the system services and framework APIs.

2. HAL (Hardware Interaction) System Services
The HAL is necessary for system services to communicate with hardware. In order to guarantee that system services function independently of particular hardware implementations, HAL acts as an abstraction layer.
For instance, Changing the Screen's Brightness:
App Request: The user adjusts brightness through the user interface.
System Service Interaction: DisplayManagerService receives the request and notifies PowerManagerService.
HAL Communication: Power HAL, which has direct hardware control, is called by PowerManagerService via Binder IPC.
Hardware Execution: By interacting with the display driver, the Power HAL modifies the brightness.
Feedback Loop: The system service updates the user interface after the HAL verifies the brightness change.
Key Takeaway: Android is flexible and adaptable because HAL guarantees that system services can function across various hardware implementations.

3. From System Services to System Services – Inter-Service Exchange
Frequently, several services collaborate to complete a task. Android's system service interactions are smooth because services communicate via Binder IPC.
Example: Intent Processing for Launching a Camera App:
An intent is triggered when the user launches the camera app.
After processing the intent, ActivityManagerService makes a request to CameraService.
Permission Validation: CameraService uses PackageManagerService to verify app permissions.
HAL Interaction: Camera HAL sets up the hardware and communicates with CameraService.
Data Processing: MediaService processes the captured images before FileManagerService ensures storage.
Key Takeaway: To effectively handle a single request, several system services work together.

Practical Example: How a Phone Call Works in AOSP
A call is initiated by the user (app layer interaction) To start a call, the Dialer app asks TelecomManager to do so.
TelephonyService receives the request from TelecomManager.
RIL and TelephonyService Interact at the Hal Layer After processing the request, TelephonyService sends it to the Radio Interface Layer (RIL). As a component of HAL, RIL is in charge of interacting with modern hardware.
RIL Gives the Modem a Command The request is converted by RIL into AT commands that the modem can comprehend. A connection is made between the modem and the network.
The call status has been updated The modem notifies RIL of the call status. TelephonyService notifies the user interface by updating the CallState.
Audio Routing & Call Connection AudioService uses the speaker or earpiece to route audio. Signal quality and LTE/VoLTE switching are managed by NetworkService.
Call Terminations: Procedure for Cleaning TelephonyService notifies RIL to end the connection when the user hangs up. TelephonyService modifies the user interface while RIL tells the modem to end the call.
Important Takeaway: Without direct app-to-hardware communication, the entire process—which includes hardware control, HAL interactions, and multiple system services—operates without a hitch.

Debugging Techniques for AOSP
Debugging AOSP builds requires an understanding of these interactions. The following are some essential debugging techniques:
Using Service Status with Dumpsys To see a list of all active services, run: adb shell dumpsys activity services
Using logcat to check logs For service activity monitoring, use: adb logcat -s ActivityManager
Verifying the Service Registration To see if a particular service is operating, run: adb shell service list
Following HAL Strace calls To monitor system calls from a service to HAL, use: strace -p

Conclusion
The framework, hardware, and apps all work together seamlessly thanks to Android System Services. They oversee essential features like connectivity, power, and security, making sure the system runs smoothly. These services maximize performance while preserving modularity and security by utilizing Binder IPC. From resource management to facilitating seamless app experiences, Android's well-organized design enables it to effectively handle complicated tasks.
Knowing these interactions demonstrates how reliable Android's architecture is across a range of devices. As we learn more about AOSP, these services continue to be essential to preserving Android's adaptability, dependability, and scalability in the rapidly changing technological environment.
#embeddedtechnology#embeddedsoftware#AOSP#HAL#Android Framework#Binder IPC#Android Telephony Stack#Android System Service
0 notes